disadvantages of nist cybersecurity frameworkair force scramble alarm sound
This would help you know at what level of compliance you are in. Train everyone who uses your computers, devices, and network about cybersecurity. NIST encourages the private sector to determine its conformity needs, and then develop appropriate conformity WebDrafted by the National Institute of Standards and Technology (NIST), this framework addresses the lack of standards when it comes to cybersecurity and provides a uniform set of rules, guidelines, and standards for organizations to use across industries. Some page levels are currently hidden.  And I'd be honored to work with Mike, to try and help NIST figure out what the industrial control securities aspects should be. Cyber security frameworks help teams address cyber security challenges, providing a strategic, well-thought plan to protect its data, infrastructure, and information systems. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. Why Use the Cybersecurity Framework? It essentially encouraged people to provide feedback. Those with a hand in creating the framework knew the importance of creating a framework to live by they shared the same vision. First of all, with it being risk-based, that means that we're trying to take a company, and focus on what their real risks are. There is no NIST cybersecurity certification. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. In this interview, recorded at the 2014 RSA Conference, Hayden explains why the risk-based approach taken by the framework nullifies one of his greatest fears heading into the NIST process, namely that it would be a compliance-driven document. Mass.gov is a registered service mark of the Commonwealth of Massachusetts. And thank you for watching this video. It should be considered the start of a journey and not the end destination.
And I'd be honored to work with Mike, to try and help NIST figure out what the industrial control securities aspects should be. Cyber security frameworks help teams address cyber security challenges, providing a strategic, well-thought plan to protect its data, infrastructure, and information systems. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. Why Use the Cybersecurity Framework? It essentially encouraged people to provide feedback. Those with a hand in creating the framework knew the importance of creating a framework to live by they shared the same vision. First of all, with it being risk-based, that means that we're trying to take a company, and focus on what their real risks are. There is no NIST cybersecurity certification. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. In this interview, recorded at the 2014 RSA Conference, Hayden explains why the risk-based approach taken by the framework nullifies one of his greatest fears heading into the NIST process, namely that it would be a compliance-driven document. Mass.gov is a registered service mark of the Commonwealth of Massachusetts. And thank you for watching this video. It should be considered the start of a journey and not the end destination.  WebNIST SP 800-53 is the information security benchmark for U.S. government agencies and is widely used in the private sector. So, I think, generally, I've been very impressed. Subcategories. Contact us to learn which security framework is best for your organization and how CyberStrong can streamline compliance and risk assessments. The CSF takes your organization out of the one-off audit compliance and risk assessment mindset, and into a more adaptive and responsive posture of managing cybersecurity risk. Working at NIST, where we have a connection to all sorts of IT experts, I saw the possibility of bridging that gap. You should also disable any features that you don't need or use, such as remote access, UPnP, or WPS, which can create security holes. That means the assessment constantly evolves to ensure all the information and best practices are updated as quickly as possible. Informa PLC is registered in England and Wales with company number 8860726 whose registered and head office is 5 Howick Place, London, SW1P 1WG. Do you think the NIST Cybersecurity Framework will be used as a measuring stick among companies? "The first concern is that it is voluntary, and money does speak loudly.
WebNIST SP 800-53 is the information security benchmark for U.S. government agencies and is widely used in the private sector. So, I think, generally, I've been very impressed. Subcategories. Contact us to learn which security framework is best for your organization and how CyberStrong can streamline compliance and risk assessments. The CSF takes your organization out of the one-off audit compliance and risk assessment mindset, and into a more adaptive and responsive posture of managing cybersecurity risk. Working at NIST, where we have a connection to all sorts of IT experts, I saw the possibility of bridging that gap. You should also disable any features that you don't need or use, such as remote access, UPnP, or WPS, which can create security holes. That means the assessment constantly evolves to ensure all the information and best practices are updated as quickly as possible. Informa PLC is registered in England and Wales with company number 8860726 whose registered and head office is 5 Howick Place, London, SW1P 1WG. Do you think the NIST Cybersecurity Framework will be used as a measuring stick among companies? "The first concern is that it is voluntary, and money does speak loudly. 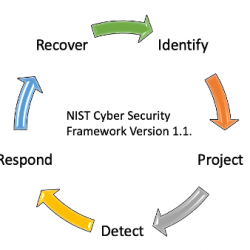 The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields. While this can seem daunting, the right tools enable a continuous compliance approach using the CSF easily. NIST has repeatedly emphasized that this is only Version 1.0 of this living document. 3) Detect - This element of the CSF encourages companies to perform an evaluation to determine if their cybersecurity measures are capable of detecting threats to the organizations computing environment. endobj
Updating your cybersecurity policy and plan with lessons learned. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware. Automate control compliance at scale with powerful, agile AI. Cookie Preferences Competition and Consumer Protection Guidance Documents, Understanding the NIST cybersecurity framework, An Inquiry into Cloud Computing Business Practices: The Federal Trade Commission is seeking public comments, FTC Orders Illumina to Divest Cancer Detection Test Maker GRAIL to Protect Competition in Life-Saving Technology Market, Hearing Before Administrative Law Judge: In re Intuit Inc. - April 3-5, 2023, NIST.gov/Programs-Projects/Small-Business-Corner-SBC, cybersecurity_sb_nist-cyber-framework-es.pdf. For many firms, and especially those looking to get their cybersecurity in order before a public launch, reaching compliance with NIST is regarded as the gold standard. In other words, worry about the high risks first, then work your way down. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works. To do this, your financial institution must have an incident response plan. For instance, in order to protect (function) your systems, you must implement software updates, install antivirus and antimalware programs, and have access control policies in place. According to London-based web developer and cybersecurity expert Alexander Williams of Hosting Data, you, about the cloud provider you use because, There isnt any guarantee that the cloud storage service youre using is safe, especially from security threats.
The National Institute of Standards and Technology (NIST) is a U.S. government agency whose role is to promote innovation and competition in the science and technology fields. While this can seem daunting, the right tools enable a continuous compliance approach using the CSF easily. NIST has repeatedly emphasized that this is only Version 1.0 of this living document. 3) Detect - This element of the CSF encourages companies to perform an evaluation to determine if their cybersecurity measures are capable of detecting threats to the organizations computing environment. endobj
Updating your cybersecurity policy and plan with lessons learned. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware. Automate control compliance at scale with powerful, agile AI. Cookie Preferences Competition and Consumer Protection Guidance Documents, Understanding the NIST cybersecurity framework, An Inquiry into Cloud Computing Business Practices: The Federal Trade Commission is seeking public comments, FTC Orders Illumina to Divest Cancer Detection Test Maker GRAIL to Protect Competition in Life-Saving Technology Market, Hearing Before Administrative Law Judge: In re Intuit Inc. - April 3-5, 2023, NIST.gov/Programs-Projects/Small-Business-Corner-SBC, cybersecurity_sb_nist-cyber-framework-es.pdf. For many firms, and especially those looking to get their cybersecurity in order before a public launch, reaching compliance with NIST is regarded as the gold standard. In other words, worry about the high risks first, then work your way down. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works. To do this, your financial institution must have an incident response plan. For instance, in order to protect (function) your systems, you must implement software updates, install antivirus and antimalware programs, and have access control policies in place. According to London-based web developer and cybersecurity expert Alexander Williams of Hosting Data, you, about the cloud provider you use because, There isnt any guarantee that the cloud storage service youre using is safe, especially from security threats. 
Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. Managing cybersecurity today is rapidly escalating to a Board- and CEO-level issue, and information security leaders must be prepared to articulate their program effectively. This article provides aggregate information on various risk assessment Copyright 2000 - 2023, TechTarget Meeting the controls within this framework will mean security within the parts of your self-managed systems but little to no control over remotely managed parts. But essentially, it's a list of checklists, and capabilities that DHS has put together, to say, "If you want to work on the Framework, you can use our checklist. Tell us why you didnt like this article. This is a new type of article that we started with the help of AI, and experts are taking it forward by sharing their thoughts directly into each section. Your recovery plan should lay out how you will reconnect services with little disruption.  The internet age has enabled an exponential increase in diversity of thought and contribution. The higher the tier, the more compliant you are.
The internet age has enabled an exponential increase in diversity of thought and contribution. The higher the tier, the more compliant you are.  That, I think, most people aren't aware of, it's more than just NIST, for example. The risks that come with cybersecurity can be overwhelming to many organizations. The first seeks to mature federal identity, credential and access management for mitigating cyberattacks, and the second combats the misconception that end users dont understand security. Instead, he said the document is focused on results for critical infrastructure providers, and its reliance on existing standards like NIST 800-53 and COBIT 5 should be seen as a positive. Notifying customers, employees, and others whose data may be at risk.
That, I think, most people aren't aware of, it's more than just NIST, for example. The risks that come with cybersecurity can be overwhelming to many organizations. The first seeks to mature federal identity, credential and access management for mitigating cyberattacks, and the second combats the misconception that end users dont understand security. Instead, he said the document is focused on results for critical infrastructure providers, and its reliance on existing standards like NIST 800-53 and COBIT 5 should be seen as a positive. Notifying customers, employees, and others whose data may be at risk.  WebFrameworks are not a new concept to cybersecurity professionals, and the benefits are immense nor do they need to be complicated to be effective. Rapidly advancing AI systems are dangerous, according to Tesla's Elon Musk and Apple's Steve Wozniak. Use this button to show and access all levels. Show due care by aligning with NISTs guidance for ransomware risk management. Now, for example, like, 800-53, is a good document, relative to business requirements, and federal mandates.
WebFrameworks are not a new concept to cybersecurity professionals, and the benefits are immense nor do they need to be complicated to be effective. Rapidly advancing AI systems are dangerous, according to Tesla's Elon Musk and Apple's Steve Wozniak. Use this button to show and access all levels. Show due care by aligning with NISTs guidance for ransomware risk management. Now, for example, like, 800-53, is a good document, relative to business requirements, and federal mandates.
Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place.
Keep in mind, though, that what they did may not necessarily work for you. Ernie, considering that this NIST Framework is entirely voluntary, do you think adoption will suffer, and are there any cares that the government could put out there, to encourage that adoption? 5G has the potential to generate billions in revenue, but MNOs must first clear up 5G applications and technologies -- such as Network engineers can use digital twins for design, testing, security and maintenance.
The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. The central idea here is to separate out admin functions for your various cloud systems, which in turn allows you a more granular level of control over the rights you are granting to your employees. CIS Controls: a concise, prioritized set of cyber practices created Ensure that there is a policy and that devices are disposed of. Encryption is the process of scrambling your data so that only authorized devices can read it. Disadvantages Implementation can take days, thus affecting productivity An improper implementation may lead to security loopholes Financial limitations may apply With cyber attacks becoming more sophisticated lately, organizations should follow the right cybersecurity frameworks and build better defenses to keep the hackers at bay.
3) Usage scenarios - The NIST CSF is a good choice for organizations just developing a cybersecurity strategy or addressing specific vulnerabilities or data breaches. The five functions of the Core are Identify, Protect, Detect, React, and Recover. The Framework is voluntary. Especially if I'm a small wastewater treatment plant, I may not spend money on my security program," said Hayden.
Companies are charged a fee to access the ISO 27001 documentation. Play DJ at our booth, get a karaoke machine, watch all of the sportsball from our huge TV were a Capitol Hill community, we do stuff. Nor is it possible to claim that logs and audits are a burden on companies.
WebThis paper deals with problems of the development and security of distributed information systems. Granted, the demand for network administrator jobs is projected to.
For example, these images can be stored on a backup virtual machine or USB flash drive. WebThe NIST CSF doesnt deal with shared responsibility. Successfully adopted by many industries, from sizable critical infrastructure firms in energy, transportation, and finance, to small and medium-sized enterprises. Web1. Want more?
The result is better communication and decision-making throughout your organization. DHS established an entity, if you will, or another directive, I'm not sure what you want to call it. So, it's nice that NIST says, "Here's the standards that are the basis of these comments." Safeguards help to mitigate the various types of threats to your financial institution. , and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. But I would hope that the larger companies would at least say, "Okay. Have formal policies for safely disposing of electronic files and old devices. Colorado Technical University ProQuest Dissertations Publishing, 2020. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their Cloud Computing and Virtualization series is a good place to start. And get a sense of where you belong in those Tiers.
Nova High School Football Tickets,
Ronson Varaflame Repair Kit,
Articles D

